7 Signs Your Business Has Outgrown Basic IMAP Email

If you’re still relying on a basic IMAP email service, your business could be exposed to security risks you don’t even see coming. IMAP might be familiar and simple, but it’s no longer fit for modern business communication—especially when it comes to protecting sensitive data and ensuring email compliance. Here are 7 warning signs it’s […]
Why Veterinary Clinics Need Dedicated IT Support Services

In today’s fast-paced, technology-driven world, veterinary clinics depend on reliable IT systems just as much as any modern medical practice. From managing patient records to processing payments, communicating with pet owners, and running diagnostic equipment, a well-functioning IT infrastructure is critical to smooth operations. Yet, many veterinary offices face frustrating tech challenges every day — […]
Why Regular Software Updates Are Critical for Business Security and IT Health

In today’s digital world, keeping your software updated isn’t just a recommendation — it’s one of the easiest and most effective ways to protect your business. Whether you’re running a small office or managing a growing team, outdated systems can open the door to cyber threats, slow down performance, and even lead to compliance issues. […]
X DDoS Attack

What Your Business Can Learn from the Recent Cyberattack on Elon Musk’s X Platform Earlier this month, Elon Musk’s X platform (formerly Twitter) was hit by a massive DDoS attack—short for Distributed Denial of Service. If you’re not familiar, a DDoS is when a swarm of compromised computers, often called a “botnet” or “zombie network,” […]
Non-Profit Data Security: Protecting Donor and Organizational Information

Data security is a critical concern for non-profits, as they handle sensitive donor, volunteer, and financial information. Many organizations assume they are less likely to be targeted by cyber threats, but in reality, cybercriminals see non-profits as easy targets due to often-limited cybersecurity measures. A data breach can lead to financial losses, damage to reputation, […]
EDR, MDR & XDR Explained: A Practical Guide for Small and Medium Business Owners

Let’s be honest—traditional antivirus software just doesn’t cut it anymore. Back in the day, installing antivirus was enough to protect your business from basic threats like spam, worms, or the occasional malicious file. Today? Not so much. Cyberattacks have evolved from amateur pranks to well-funded, highly organized campaigns aimed at stealing data, holding your systems […]
Phishing Scams Are Evolving: Here’s How to Stay Ahead
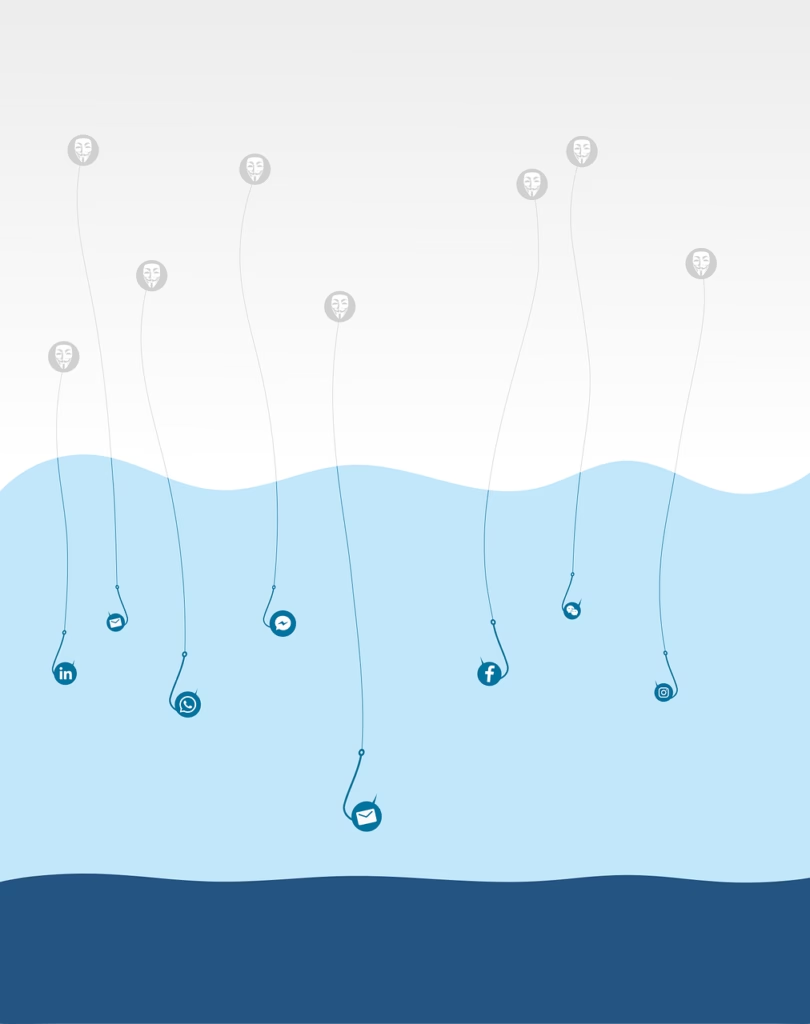
Introduction Phishing scams have become more sophisticated than ever, leveraging AI, deepfake technology, and advanced social engineering tactics to deceive even the most vigilant individuals. Cybercriminals continuously refine their methods, making it essential for businesses and employees to stay informed and protected. This article explores the latest phishing techniques, how to identify them, and proactive […]
Top 10 Most Destructive Computer Viruses of All Time

Introduction In the digital age, computer viruses have become a significant threat to individuals and organizations alike. These malicious programs can corrupt data, steal sensitive information, and disrupt essential services. The impact of computer viruses extends beyond mere technical glitches; they can result in substantial financial losses, damage reputations, and even jeopardize national security. Understanding […]
How Managed IT Services Enhance Cybersecurity
I. Introduction In today’s digital age, cybersecurity threats are escalating at an unprecedented rate. Businesses of all sizes are grappling with sophisticated cyber attacks that can compromise sensitive data, disrupt operations, and damage reputations. The increasing cost and impact of data breaches highlight the urgent need for robust cybersecurity measures. Protecting sensitive information and maintaining […]

